- Furuno Vdr Software Download
- Furuno Vdr Playback Software
Some Furuno GPS receivers have an internal week number rollover on June 20th this year. After rollover the date is no longer presented correctly. We recommend upgrade to a successor model.
The GPS system’s time and date is synchronized according to a different scale than coordinated universal time (UTC). The GPS date is calculated based on a known start date and an interval of 1023 weeks. After 1023 weeks, the date is reset to the first date in the system’s week 0. When this happens in the satellite system it is often referred to as an external GPS week number rollover. In addition, all GPS receivers have their own internal week number rollover that follows the same principle, but with a different date as their first date in their week 0. Newer GPS receivers usually handle both the external satellite system’s rollover and the internal rollover in their own software. Older models may need specific software update, or replacement if software update is not possible.
INTERNAL GPS ROLLOVER JUNE 20th 2021
Some Furuno GPS receivers have an internal week number rollover on June 20th this year. After the rollover, the date will no longer be presented correctly. The list below includes the models offered to the Norwegian market. For these models software update is not possible. Our recommendation is that they are replaced by their successor model.
CD-ROM drive is needed to install this software. 1.2 Software Installation 1. Set the Live Player software CD in the CD drive. Open the Explorer folder to view the files on the CD. Double-click the Setup.exe icon to start the installation of the Live Player. The setup wizard. Play back and Live play are available with optional software. Power Use: 110 VAC or 220 VAC Receiver Type: N/A Related Material Furuno VR3000 Voyage Data Recorder Brochure Furuno VR3000 Voyage Data Recorder Operations Manual The Furuno VR3000 is designed for newly constructed cargo ships greater than 3,000 gross tons and passenger ships. Fax: +81 (0)7, 66-4622 URL: www.furuno.co.jp TRADE MARK REGISTERED MARCA REGISTRADA S-VDR VR-3000S VDR VR-3000. The VR-3000/S is a Voyage Data Recorder/Simplified Voyage Data Recorder, which fully complies with IMO A861(20) and IEC 61996 and IEC 60945, and IMO MSC. 163(78) and IEC 61996-1/2. Software application, Liveplayer Pro for. This software extracts and displays the data accumulated from the VR-7000, in real time, on the networked PC screen. Also, the data can be replayed for a more thorough data analysis at a later date. Remote Alarm Panel At-a-glance recognition of VDR status with minimal operation. Revised performance standards of VDR MSC.333 (90).

Presentation of position may also be affected. To correct this the equipment can be turned off and restarted. It is also possible to run a corrective command from the menu.
To remedy incorrect presentation of position data, you can run the command specified for each device:
GPS | System restart command | Replacement model |
| GP-80 | [MENU]→ [9]→[9]→[Clear GPS]→[Yes]→[ENT] | Furuno GP-170
Rattmerket GPS/DGPS med mulighet også for GLONASS/DGLONASS og kombinert GPS/GLONASS |
| GP-90/DUAL | [MENU]→ [9]→[9]→[Clear GPS]→[Yes]→[ENT] | Furuno GP-170
Rattmerket GPS/DGPS med mulighet også for GLONASS/DGLONASS og kombinert GPS/GLONASS |
| GP-1650W/WD/WDF/WF | [MENU]→ [CONFIGURATION]→[MEMORY/TRIP CLEAR]→[CLEAR GPS MEMORY] | Furuno GP-1871F |
| GP-1850W/WD/WDF/WF | [MENU]→ [CONFIGURATION]→[MEMORY/TRIP CLEAR]→[CLEAR GPS MEMORY] | Furuno GP-1971F |
| GP-32/37 | [MENU]→ [ERASE]→[ENT]→[GPS DATA?]→[ENT] | Furuno GP-39 |
| GP-320B | When NAV1 is connected, please check [GPS SENSOR SETTINGS] | Furuno GP-330B |
by Ruben Santamarta @reversemodeIn 2014, IOActive disclosed a series of attacks that affect multiple SATCOMdevices, some of which are commonly deployed on vessels. Although there is nodoubt that maritime assets are valuable targets, we cannot limit the attacksurface to those communication devices that vessels, or even large cruise ships,are usually equipped with. In response to this situation, IOActive providesservices to evaluate the security posture of the systems and devices that makeup the modern integrated bridges and engine rooms found on cargo vessels andcruise ships. [1]
There are multiple facilities, devices, and systems located on ports andvessels and in the maritime domain in general, which are crucial to maintainingsafe and secure operations across multiple sectors and nations.
Port security refers to protecting all of these assets from acts of piracy,terrorism, and other unlawful activities, such as smuggling. Recent activity appearsto demonstrate that cyberattacks against this sector may have beenunderestimated. As threats evolve, procedures and policies must improve to takethese new attack scenarios into account. For example, https://www.federalregister.gov/articles/2014/12/18/2014-29658/guidance-on-maritime-cybersecurity-standards
This blog post describes IOActive’s research related to one type of equipmentusually present in vessels, Voyage Data Recorders (VDRs). In order tounderstand a little bit more about these devices, I’ll detail some of theinternals and vulnerabilities found in one of these devices, the FurunoVR-3000.
(http://www.imo.org/en/OurWork/Safety/Navigation/Pages/VDR.aspx ) A VDR isequivalent to an aircraft’s ‘BlackBox’. These devices record crucial data, suchas radar images, position, speed, audio in the bridge, etc. This data can be usedto understand the root cause of an accident.
Several years ago, piracy acts were on the rise. Multiple cases were reportedalmost every day. As a result, nation-states along with fishing and shippingcompanies decided to protect their fleet, either by sending in the military or hiringprivate physical security companies.
On February 15, 2012, two Indian fishermen were shot by Italian marinesonboard the Enrica merchant vessel, who supposedly opened fire thinking theywere being attacked by pirates. This incident caused a serious diplomaticconflict between Italy and India, which continues to the present. https://en.wikipedia.org/wiki/Enrica_Lexie_case
'Mysteriously', the data collected from the sensors and voice recordingsstored in the VDR during the hours of the incident was corrupted, making ittotally unusable for authorities to use during their investigation. As this story, from Indian Times, mentions theVDR could have provided authorities with crucial clues to figure out whatreally happened.
http://timesofindia.indiatimes.com/city/chennai/Lost-voice-data-recorder-may-cost-India-Italian-marines-case/articleshow/18942389.cms
Curiously, Furuno was the manufacturer of the VDR that was corrupted inthis incident. This Kerala High Court’s document covers this fact: http://indiankanoon.org/doc/187144571/ However, we cannot say whether the model Enrica Lexie was equipped withwas the VR-3000. Just as a side note, the vessel was built in 2008 and theFuruno VR-3000 was apparently released in 2007.
Just a few weeks later, on March 1, 2012, the Singapore-flagged cargoship MV. Prabhu Daya was involved in a hit-and-run incident off the KeralaCoast. As a result, three fishermen were killed and one more disappeared andwas eventually rescued by a fishing vessel in the area. Indian authoritiesinitiated an investigation of the accident that led to the arrest of the MV.Prabhu Daya’s captain.
During that process, an interesting detail was reported in several Indiannewspapers.
http://www.thehindu.com/news/national/tamil-nadu/voyage-data-recorder-of-prabhu-daya-may-have-been-tampered-with/article2982183.ece
From a security perspective, it seems clear VDRs pose a reallyinteresting target. If you either want to spy on a vessel’s activities ordestroy sensitive data that may put your crew in a difficult position, VDRs arethe key.
Understanding a VDR's internals can provide authorities, or third-parties,with valuable information when performing forensics investigations. However, theability to precisely alter data can also enable anti-forensics attacks, asdescribed in the real incident previously mentioned.
As usual, I didn’t have access to the hardware; but fortunately, Iplayed some tricks and found both firmware and software for the target VDR. Thedetails presented below are exclusively based on static analysis and user-modeQEMU emulation (already explained in a previous blog post). [2]
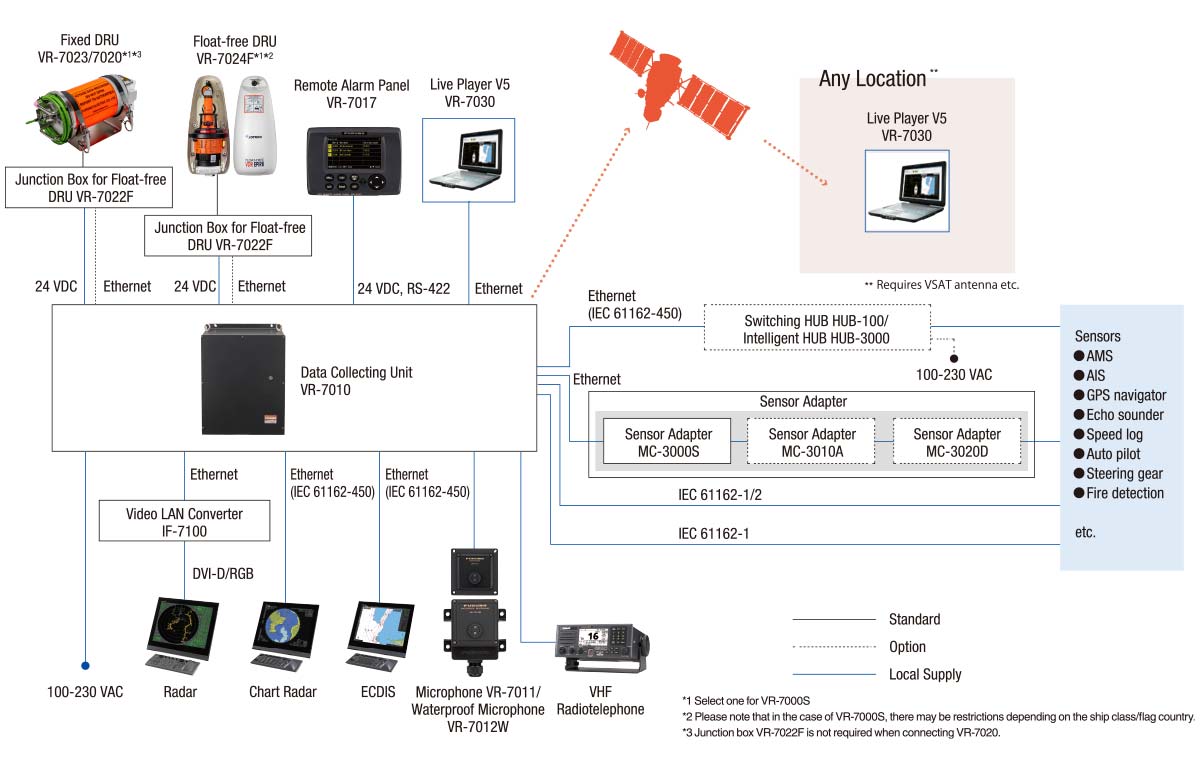
Figure: Typical architecture of aVR-3000
Basically, inside the Data Collecting Unit (DCU) is a Linux machine withmultiple communication interfaces, such as USB, IEEE1394, and LAN. Also insidethe DCU, is a backup HDD that partially replicates the data stored on the DataRecording Unit (DRU). The DRU is protected against aggressions in order tosurvive in the case of an accident. It also contains a Flash disk to store datafor a 12 hour period. This unit stores all essential navigation and status datasuch bridge conversations, VHF communications, and radar images.
The International Maritime Organization (IMO) recommends that all VDRand S-VDR systems installed on or after 1 July 2006 be supplied with anaccessible means for extracting the stored data from the VDR or S-VDR to alaptop computer. Manufacturers are required to provide software for extractingdata, instructions for extracting data, and cables for connecting between a recordingdevice and computer.
Furuno Vdr Software Download
The following documents provide more detailed information:
http://www.furunousa.com/ProductDocuments/VR3000%20Data%20Extraction%20Instructions%20for%20version%202.xx.pdf
http://www.furuno.fr/Multimedia/VR3000_VR3000S_OME-G1.pdf
After spending some hours reversing the different binaries, it was clearthat security is not one of its main strengths of this equipment. Multiple servicesare prone to buffer overflows and command injection vulnerabilities. The mechanismto update firmware is flawed. Encryption is weak. Basically, almost the entiredesign should be considered insecure.
Take this function, extracted from from the Playback software, as anexample of how not to performauthentication. For those who are wondering what 'Encryptor' is, just a word:Scytale.
Digging furtherinto the binary services we can find a vulnerability that allowsunauthenticated attackers with remote access to the VR-3000 to executearbitrary commands with root privileges. This can be used to fully compromisethe device. As a result, remote attackers are able to access, modify, or erasedata stored on the VDR, including voice conversations, radar images, andnavigation data.
VR-3000’sfirmware can be updated with the help of Windows software known as 'VDRMaintenance Viewer' (client-side), which is proprietary Furuno software.
The VR-3000firmware (server-side) contains a binary that implements part of the firmwareupdate logic: ‘moduleserv’
This servicelistens on 10110/TCP.
Internally, bothserver (DCU) and client-side (VDR Maintenance Viewer, LivePlayer, etc.) use aproprietary session-oriented, binary protocol. Basically, each packet maycontain a chain of 'data units', which, according to their type, will containdifferent kinds of data.
Figure: Some ofthe supported commands
'moduleserv' severalcontrol messages intended to control the firmware upgrade process. Let's analyze how it handles a'SOFTWARE_BACKUP_START' request:
An attacker-controlledstring is used to build a command that will be executed without being properly sanitized.Therefore, this vulnerability allows remote unauthenticated attackers toexecute arbitrary commands with root privileges.

Atthis point, attackers could modify arbitrary data stored on the DCU in order to,for example, delete certain conversations from the bridge, delete radar images,or alter speed or position readings. Malicious actors could also use the VDR tospy on a vessel’s crew as VDRs are directly connected to microphones located,at a minimum, in the bridge.
However,compromising the DCU is not enough to cover an attacker’s tracks, as it onlycontains a backup HDD, which is not designed to survive extreme conditions. Thekey device in this anti-forensics scenario would be the DRU. The privilegedposition gained by compromising the DCU would allow attackers to modify/deletedata in the DRU too, as this unit is directly connected through an IEEE1394interface. The image below shows the structure of the DRU.
BeforeIMO's resolution MSC.233(90) [3], VDRs did not have tocomply with security standards to prevent data tampering. Taking into account thatwe have demonstrated these devices can be successfully attacked, any datacollected from them should be carefully evaluated and verified to detect signsof potential tampering.
IOActive,following our responsible disclosure policy, notified the ICS-CERT about thisvulnerability in October 2014. The ICS-CERT, working alongside the JPCERT/CC,were in contact with Furuno and were able to reproduce and verify thevulnerability. Furuno committed to providing a patch for their customers'sometime in the year of 2015.' IOActive does not have furtherdetails on whether a patch has been made available.
--------------
Furuno Vdr Playback Software
1.http://www.ioactive.com/alerts/maritime-vessel-ship-security-assurance.html
2.http://blog.ioactive.com/2013/09/emulating-binaries-to-discover.html
3.http://www.imo.org/en/KnowledgeCentre/IndexofIMOResolutions/Documents/MSC%20-%20Maritime%20Safety/333(90).pdf
Source: lmth.egayov-otni-gnikcah-ytiruces-emitiram/21/5102/moc.evitcaoi.golb


